4
Core Technology

ONE
Based on the GG20 protocol, the TEE trusted environment container (such as Intel SGX, AMD Trustzone, etc.) on the device is used to store private key fragments, thereby eliminating the risk of complete private key disclosure.
TWO
The threshold-threshold signature scheme has its own recasting mechanism, which can ensure flexible "reshuffle". Under the condition that the public key remains unchanged, each private key fragment can be replaced arbitrarily.
THREE
A non-interactive signature mechanism is adopted, and each round of interactive information will only generate a signature once, which can be discarded after use to ensure the privacy of information interaction.
FOUR
By introducing a zero-knowledge proof algorithm, each signature interaction can verify the correctness of member behavior, helping the system identify and punish those malicious members.
Underlying technical features

Cryptography-based algorithmic security barriers
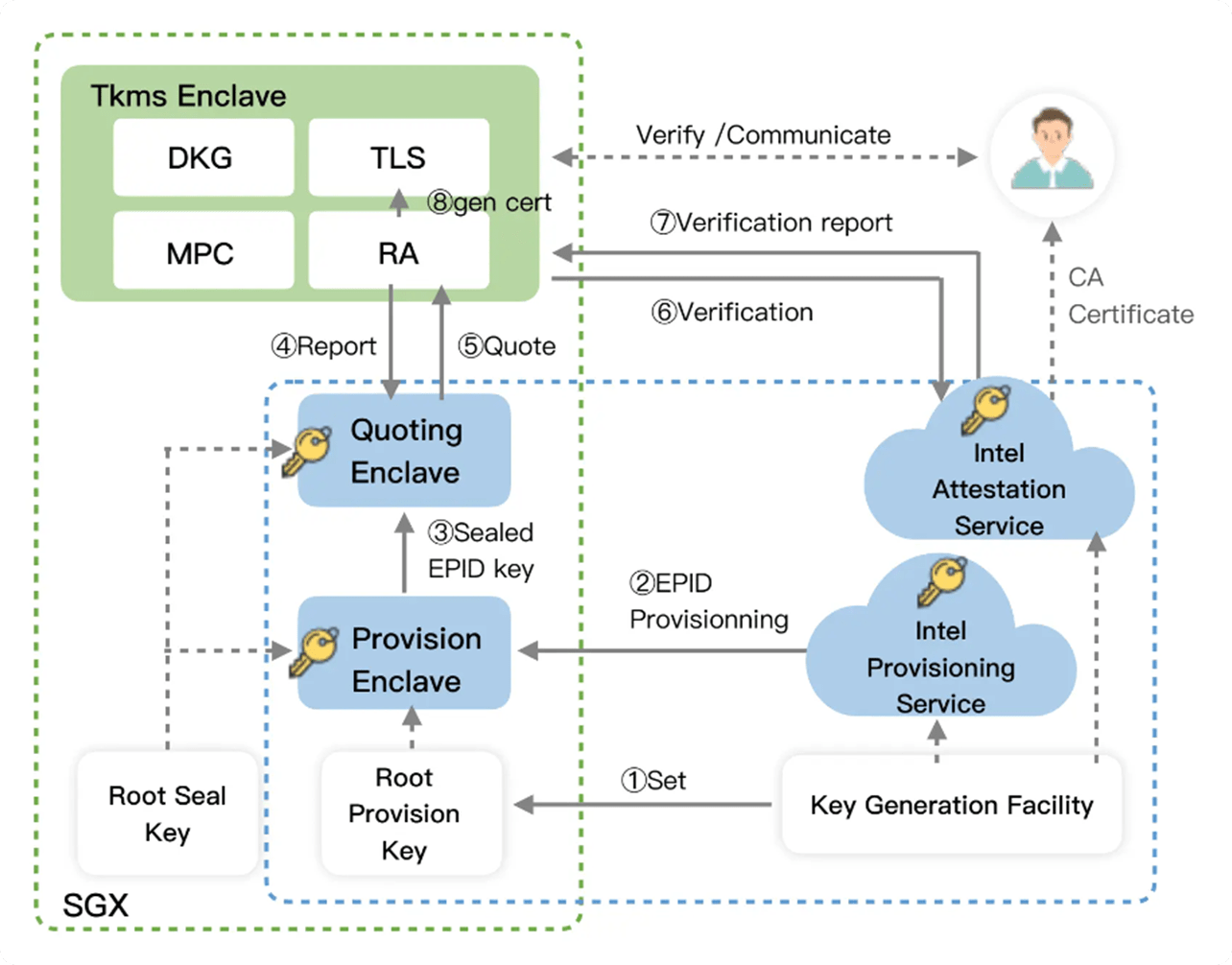
By adopting MPC-TSS gated signature scheme, the private key is completely generated by the machine in a hardware-level secure environment (TEE), sharded and stored in a distributed manner, avoiding human intervention and isolating the risk of private key exposure.
It supports recasting mechanism, which can ensure that the private key can still be reconfigured in the event of single-point failure of the device to protect the account security; adopting non-interactive signature mechanism, each round of interactive information will only produce one signature, which will be discarded after use to ensure the privacy of information interaction, thus enhancing the cost and difficulty of hacker attacks.
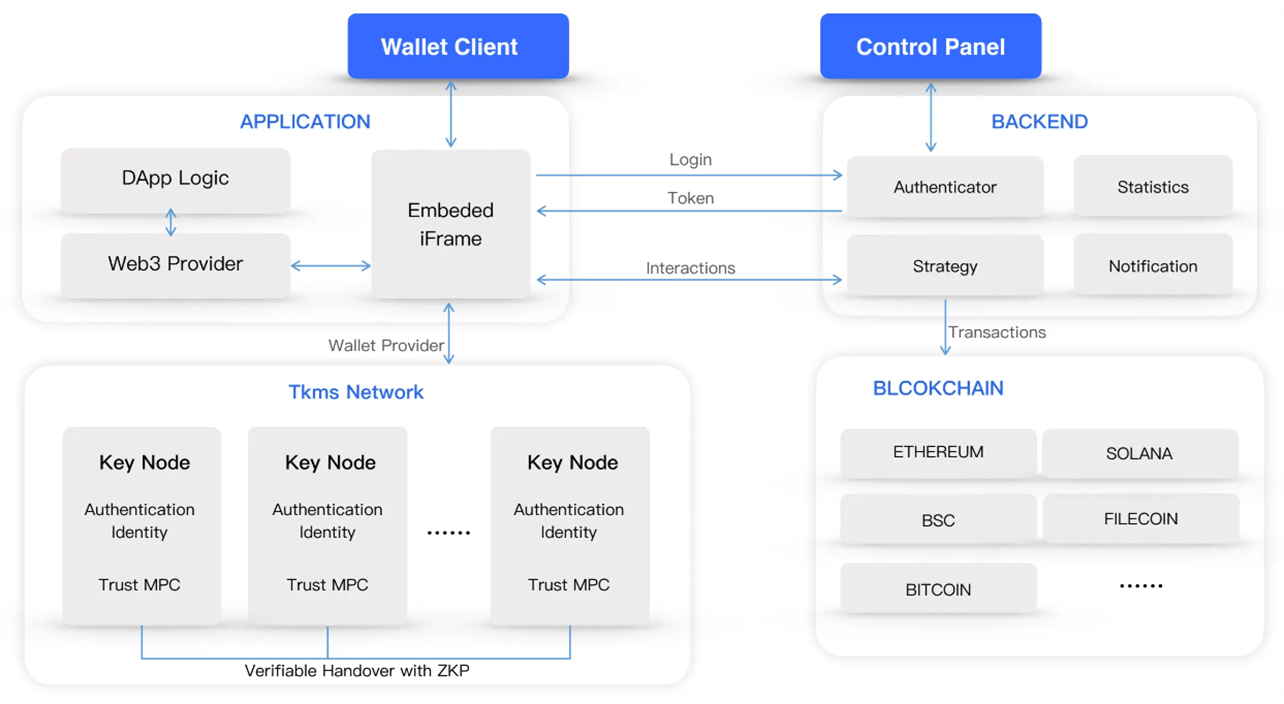

Flexible and efficient security policy configuration
In terms of account security, on top of the existing verification code and password login, support users to open fingerprint recognition, Google Authenticator and other ways to enhance the account security level.
In terms of asset security, it supports users to configure transfer whitelist, set maximum transaction limit, etc. to customize a set of security policy that is entirely their own, so that when encountering a very small probability of risk events, the asset loss level of the account can still be reduced to a manageable level.
In terms of organizational security, the signature policy of the condomnium wallet can be adjusted at any time, and risky members can be replaced in a timely manner by consensus of the majority of the members, thus reducing the risk of accidents occurring to the shared assets.

Easier registration, easier retrieval
It supports one-click account login with users' usual email and third-party account authorization, and it supports switching to wallet account system senselessly without recording tedious helper words, supporting senseless login and senseless payment; we provide sweeping code authorization method, which is convenient for users to quickly switch login between different devices; at the same time, it also provides two backup recovery methods, email and Microsoft Onedrive, so that users can still recover their original account on new devices when their usual devices are lost. If users lose their usual devices, they can still easily restore the original account login on the new device.

